Agentless Desktop SSO
The OptimalCloud Agentless Desktop Single Sign-on (SSO) feature allows users that are identified as being on-premise (or via VPN) and connected to their local AD Forest, to sign-on using their Windows Desktop Credentials via Integrated Windows Authentication (IWA).
The process flow is as follows:
- An end-user client attempts to access a protected resource in The OptimalCloud. The OptimalCloud will check to see if this feature is enabled and all settings are present. If the users IP Address is in the defined IP Range list it will direct the user’s browser to send a Kerberos Ticket to the OptimalCloud (if possible) (401).
- If the browser is properly configured to trust The OptimalCloud site, the browser will obtain a Kerberos Ticket from the on-premise Key Distribution Center (KDC) and send that Ticket to The OptimalCloud.
- The OptimalCloud will then decode/decrypt the Ticket, validate the user, and if successful, will generate a session and allow the user to continue to the requested page/process.
- If the Ticket fails to be decrypted or is somehow invalid, the user will continue to see the default login or hrd page.
Client Configuration
Create a Service Account
In order to fully support IWA, you must create a new service account within your on-premise AD forest.
- The name and password can be any value you choose.
- No permissions need to be granted to this account.
- Enable the “This account supports Kerberos AES 256 bit encryption” setting for this account.
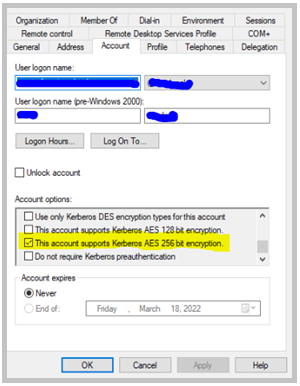
The following steps will automatically generate the required SPN’s as needed.
Anytime that you change the password on the defined service account, you must generate a new KeyTab file and upload it in the OptimalCloud.
Generate a KeyTab File
In order to fully support IWA, you must create and upload a KeyTab file. This process configures the SPN with the Service Account for proper decryption of the Kerberos Ticket.
In order to generate thy KeyTab file, you need to run the following commands on your on-premise AD system:
- ktpass /princ HTTP/{full site url@domain} /mapuser {NETBIOS_NAME}\{ServiceAccountName} /pass {PasswordForServiceAccountHere} /out TheOptimalCloud.keytab /crypto all /PTYPE KRB5_NT_PRINCIPAL /mapop add
Example:
ktpass /princ HTTP/contoso.theoptimalcloud.com@CONTOSO.COM /mapuser CONTOSO\toc_serviceacct /pass MyStrongPasswordHere /out TheOptimalCloud.keytab /crypto all /PTYPE KRB5_NT_PRINCIPAL /mapop add
- Run the following command for each data-center in your deployment. The full list of data-center url’s may be obtained from Optimal IdM.
ktpass /princ HTTP/{data-center url}@{domain} /mapuser {NETBIOS_NAME}\{ServiceAccountName} /pass {PasswordForServiceAccountHere} /out TheOptimalCloud.keytab /crypto all /PTYPE KRB5_NT_PRINCIPAL /mapop add /in TheOptimalCloud.keytab
The output file generated from the commands above, TheOptimalCloud.keytab, will be used when configuring the OptimalCloud.
Configure Browsers
The browsers used by your company need to be configured to support IWA with The OptimalCloud.
Create a Group Policy Object (GPO) in Windows that includes enabling IWA for the browsers and to add your Tenant’s URL into the “local intranet” trusted zone. (ex. https://contoso.theoptimalcloud.com)
The following browser configuration changes are required.
- Internet Explorer - Nothing additional required on either Windows or Mac.
- Safari - Nothing additional required.
- Chrome - Must have ‘AuthServerAllowlist’ set with your Tenant’s hostname (ex. contoso.theoptimalcloud.com)
- Edge (Chromium) - Must have ‘AuthServerAllowlist’ set to your Tenant’s hostname (ex. contoso.theoptimalcloud.com)
- Firefox - Must have “network.negotiate-auth.trusted-uris” set to your Tenant’s hostname (ex. contoso.theoptimalcloud.com)
The OptimalCloud Configuration
The OptimalCloud Agentless Desktop SSO may be configured for the whole Tenant or for an Organization. You may enable it for the Tenant and also for a specific organization. The Domains and IP Ranges specified for each must not be the same.
Enable ADSSO for your Tenant
To enable Agentless Desktop SSO for your Tenant, go to the My Company Account/Tenant application on the Administration tab.
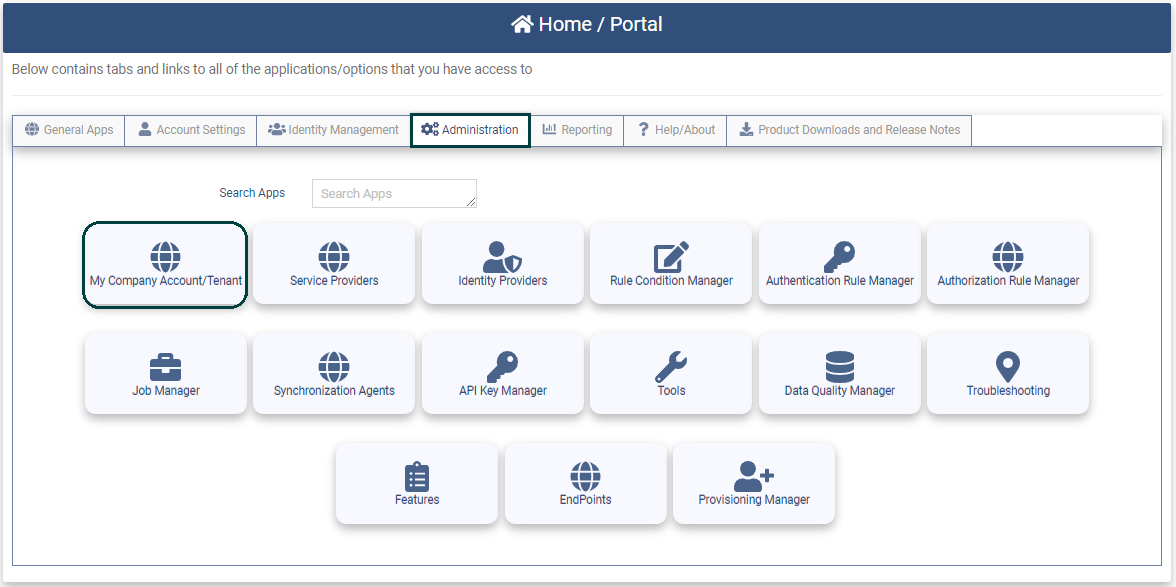
Clicking on the application will present the Company Account/Tenant Details page.
Click on the Agentless Desktop SSO tab.
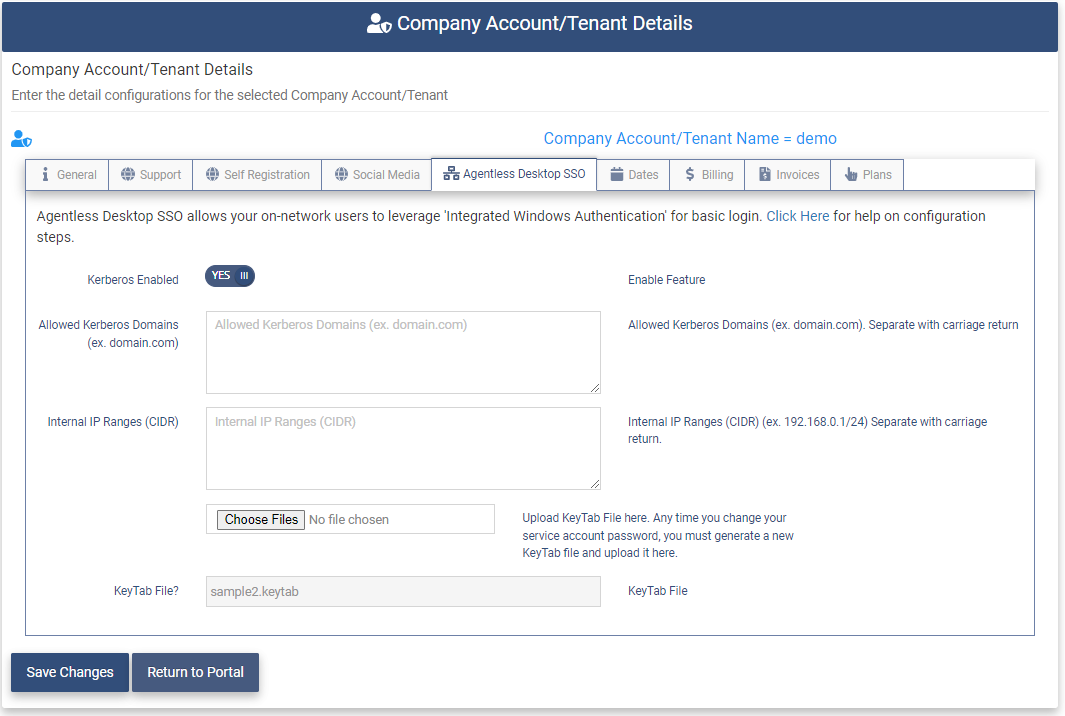
Set the following fields.
- Kerberos Enabled - Set this field to “YES” to enable Agentless Desktop SSO for the Tenant. This step must be done to allow Agentless Desktop SSO for the Tenant or for an Organization.
- Allowed Kerberos Domains - the list of domains in your local AD Forest that the OptimalCloud will accept Kerberos Tickets from (separated by a carriage return). (ex. contoso.com)
- Internal IP Ranges (CIDR) - the OptimalCloud will perform IWA for users in this list of CIDR IP Ranges. (ex. 192.168.0.1/24)
Click the 
Click the 
Enable ADSSO for an Organization
To enable Agentless Desktop SSO for an organization perform the following steps.
- Set the Enable Kerberos field for the Tenant if it has not been set. See the Enable for your Tenant section above.
- Create a Service Account within the organization's AD Forest.
- Create a KeyTab File for use for this organization. See the Generate a KeyTab File section above.
You must generate a separate Service Account and KeyTab File for each organization that has different domains.
- Next go to the Organization Manager application on the Identity Management tab.
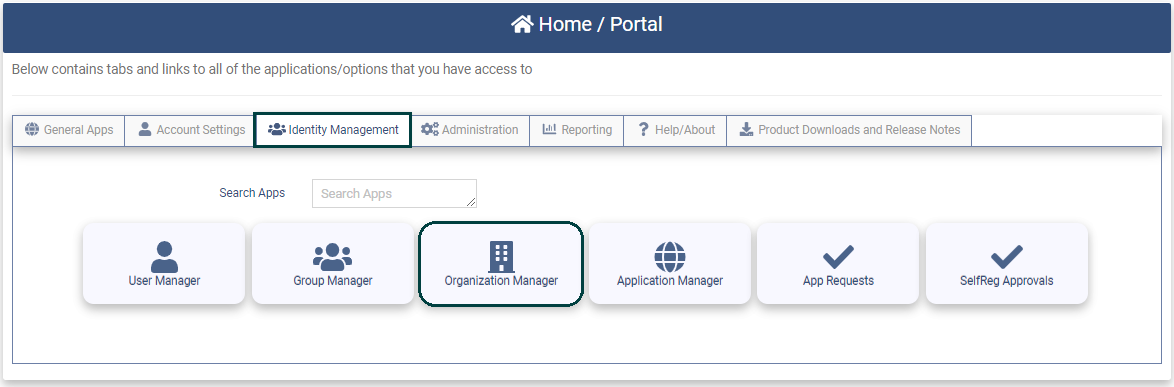
Clicking on the application will present the Organization Manager page.
Click the 
Click on the Agentless Desktop SSO tab.
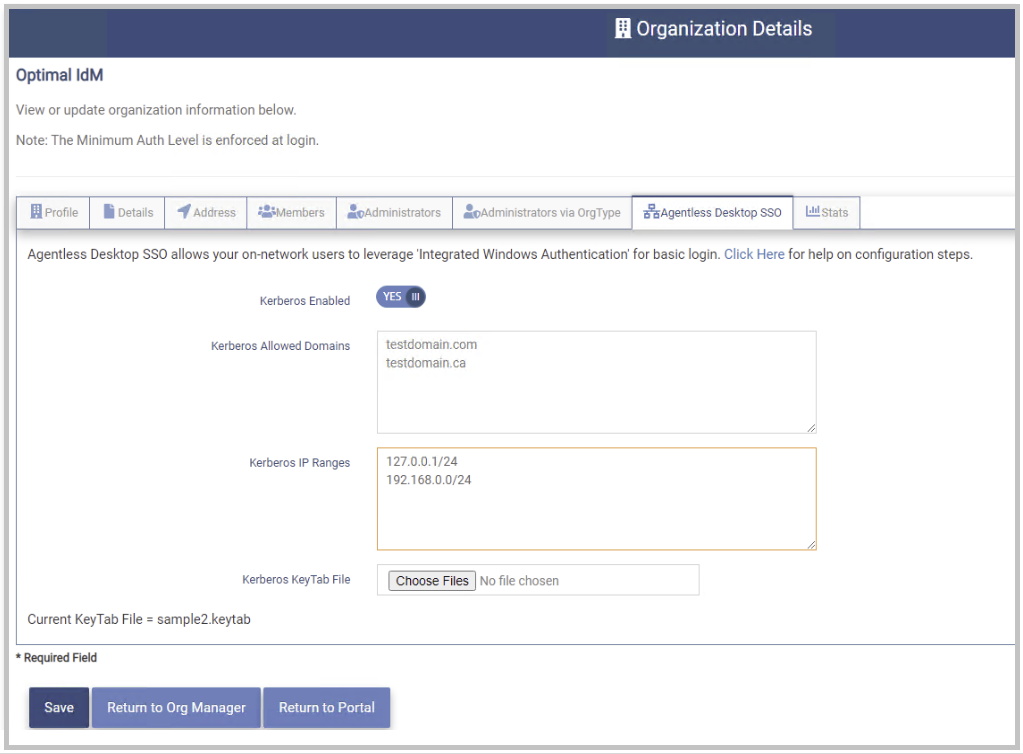
Set the following fields.
- Kerberos Enabled - Set this field to “YES” to enable Agentless Desktop SSO for this organization.
- Allowed Kerberos Domains - the list of domains in the organization's local AD Forest that the OptimalCloud will accept Kerberos Tickets from (separated by a carriage return). (ex. contoso.com)
- Internal IP Ranges (CIDR) - the OptimalCloud will perform IWA for users in this list of CIDR IP Ranges. (ex. 192.168.0.1/24)
The list of Domains and IP Ranges set for this organization MUST NOT be the same as those set for the Tenant or any other organization
Click the 
Click the 
Notes
- Troubleshooting Kerberos: Enable Kerberos logging -- https://support.microsoft.com/en-us/help/262177/how-to-enable-kerberos-event-logging
- Alternative to Agentless Desktop SSO: Optimal IdM, also supports an on-premise solution that support Desktop SSO, but it requires an on-premise server to host the agent. Please reach out to Optimal IdM Support for more information on this feature.